I had just wrapped up some internal Tidelift research on open source software supply chain compromises a few weeks ago when I saw PyPI's announcement about requiring 2FA on critical PyPI projects.
It seemed like great news for the open source community—free hardware keys too! 🔑—especially since npm and RubyGems have been working towards similar aspirations.
But then some fallout occurred, and we saw a maintainer react to the news by "de-critical'ing" their project by deleting older versions. Luckily the versions were restored in the end.
It was a bit disheartening to see a maintainer react so negatively to 2FA. There's no way for the public to know how secure a maintainer's password is, so 2FA is a better level of protection as well as a nice assurance for downstream users.
Based on the open data that I've aggregated (shout out to the researchers uncovering these attacks!) it seems that the issue of repository security needs to be more public.
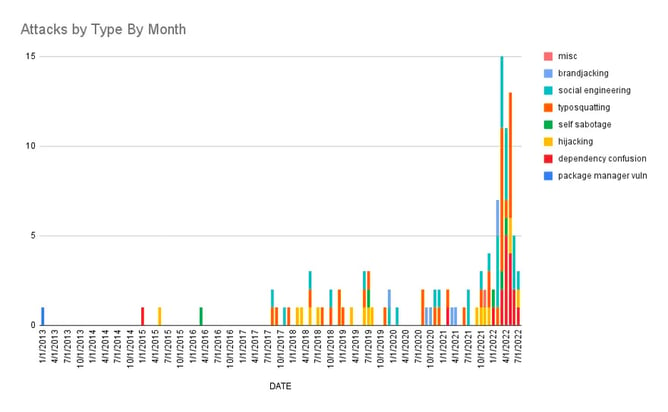
Graphing the data
I've categorized the OSS repo compromises I found into several categories:
- typosquatting
- hijacking (e.g. account takeovers)
- dependency confusion
- social engineering (e.g. generally tricking people into using your malware)
- self-sabotage
- package manager vulnerability
The majority of repos that I found compromised data for were npm and PyPI, with a bit of RubyGems:
Data caveats 🧐
One has to consider some major caveats here:
- attacks are only found where/when people are looking
- this is only the public data we've found; there are certainly unpublished attacks out there
- some of these attacks are actually grouped findings involving separate actors
- on a positive note, occasionally these attacks are just pen-testers and researchers
Ecosystem 📈
It's clear that supply chain attacks have intensified (and package hijackings haven't gone away), but thanks to the work in the past four-ish years to repository contributors, we've seen:
- 2FA and API key improvements on npm, Nuget, PyPI and RubyGems
- repository-signed packages on npm and PyPI
- author-signed packages fully supported on Nuget, and being discussed for PyPI/RubyGems
Please shout out any other big repo security milestones I've missed here on Twitter, or if you have thoughts/feelings on these measures.
Also...thanks to our Tidelift partnered maintainers (we call them lifters) for generally taking this stuff seriously too. 🥲



 50 Milk St, 16th Floor, Boston, MA 02109
50 Milk St, 16th Floor, Boston, MA 02109