In December of 2021, Tidelift fielded our annual survey of technologists who use open source to build applications at work. Nearly 700 people shared how they use open source software today, what holds them back, and what tools and strategies help them use it even more effectively.
In this post, we share the sixth of seven key findings. If you don’t want to wait for the rest of the results, you can download the full survey report right now at the link below.
In May of last year, the White House released an executive order on improving the nation’s cybersecurity, in part influenced by the software supply chain vulnerability that impacted SolarWinds and its customers, including many in the United States government. The executive order was seen by some as a strategy to use the purchasing power of the government to improve the way cybersecurity is addressed around the world.
Over the past year, the executive order has increased momentum inside and outside of government around the importance of applications having up-to-date software bills of materials (SBOMs) and has technology leaders asking themselves tough questions about how they can improve the health and security of the open source software supply chain.
Many organizations are now investigating how to document and maintain an SBOM for their software applications, and they are also researching how to meet other requirements like attesting to the security and provenance of the open source software they are shipping as part of their products.
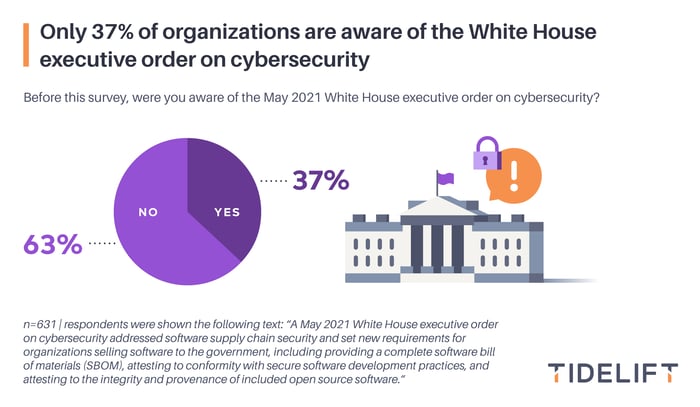
In this year’s survey, we wanted to see if there was broad awareness around the White House executive order on cybersecurity and some of the requirements it imposes on organizations.
Just over one third of respondents (37%) were aware of the executive order while almost two thirds (63%) were not.
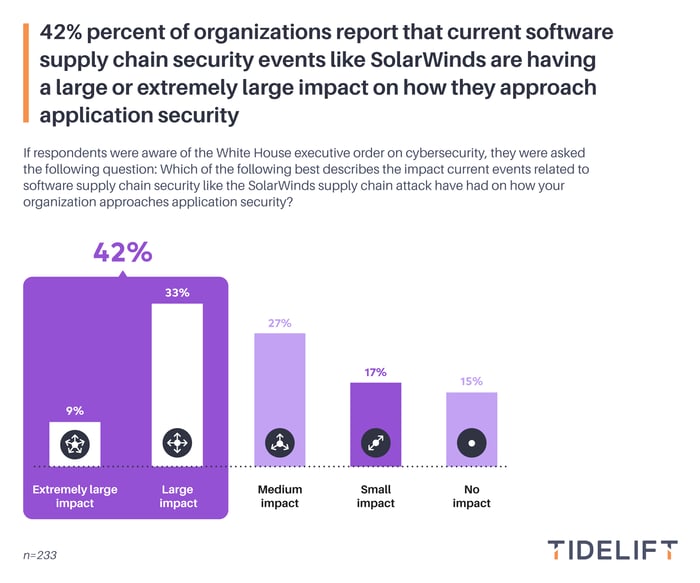
We also wanted to see if their organizations’ approach to managing application security has been impacted by recent software supply chain security events like the SolarWinds attack, so we asked this as a follow up question to those respondents aware of the White House executive order on cybersecurity.
Not surprisingly, of these organizations, 42% report that current software supply chain security events like SolarWinds are having a large or extremely large impact on how they approach application security. Only 15% of organizations see no impact at all.
We hope you found some useful and actionable information in this blog post. If you’d like to get notified as future posts come out, please sign up for our blog digest here. Or if you don’t want to wait, download the full survey results today!


 50 Milk St, 16th Floor, Boston, MA 02109
50 Milk St, 16th Floor, Boston, MA 02109