Welcome to the May 2021 edition of the Tidelift product update, or Pupdate for short! The Pupdate is our monthly rundown of new features and enhancements in the Tidelift product, and there’s a picture of a dog at the end, as a special treat for those who read the whole thing.
Earlier this week, I had the opportunity to do a webinar with our good friends at JFrog. In case you missed it, I spoke about the rise of open source software supply chain attacks and how to keep enterprises safe. When I started at Tidelift, we used to reference the now infamous Equifax breach as a worst-case scenario for an enterprise. Unfortunately, these supply chain attacks are becoming increasingly more frequent.
Just yesterday, the Biden administration released a new executive order about securing the U.S. federal government’s software supply chain, so this is a dynamic problem, changing every day.
This month, I am going to highlight three new features that can help your organization manage your open source better while minimizing the risk of open source software supply chain attacks.
#1: Understand your catalog and projects’ health
Working to get all of your projects using only approved open source components is a journey. One of the first steps when you begin using the Tidelift Subscription is to get a clear picture of the open source you are using today. With the Tidelift Subscription, you can quickly get a software bill of materials showing the open source you are using today, and how healthy and well managed it is.
If you have never tried to manage open source before, the skeletons you see in the closet might leave you shaking in your boots. 😱 That first look at the accumulated technical debt can be scary and overwhelming—but don’t worry, we got you! With the Tidelift Subscription, we help you prioritize your time and give you recommendations to help you can focus on the most urgent issues first.
This month, we launched this new overview to give you an at-a-glance view of catalog and project health.
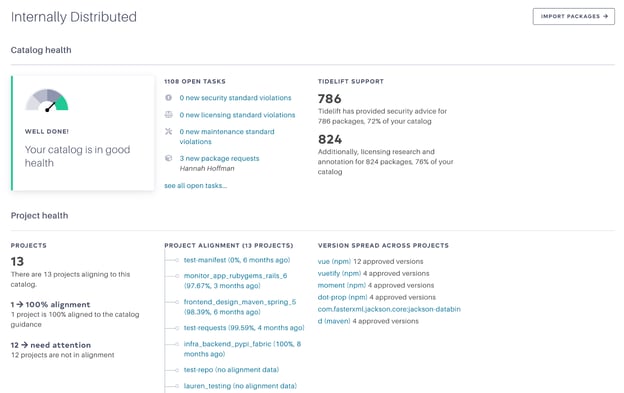
I recommend paying attention to two metrics when you’re getting started:
- Average alignment should be going up. You want more and more of your developers’ projects to come into full alignment with your organization’s catalog over time.
- Number of catalog tasks should be going down. You want to make sure that you are completing tasks, such as reviewing security vulnerabilities and responding to package requests from developers.
If you stay focused on these outcomes, you will be managing your open source like a champ, paying down accumulated technical debt quickly, and will dramatically decrease your organization’s risk of being targeted by open source software supply chain attacks.
#2: Manage your inner source with Tidelift catalogs
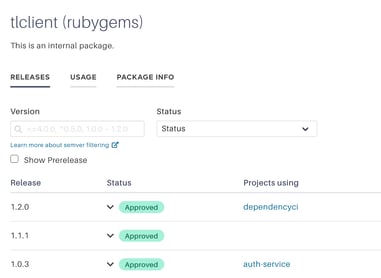
You can now include internally developed open source packages in your Tidelift catalog! This is a much-anticipated feature, and we are so pleased to provide you with the ability to make decisions on packages that are only developed and used internally within your organization.
Tidelift creates a bill of materials for each of your projects and keeps it up-to-date. If the Tidelift Subscription doesn’t recognize a package, we will automatically label it as internal. You can now view where each version of the package is being used across the organization and deny or approve specific versions. We have used this at Tidelift to indicate when older versions of our design system library are no longer acceptable to use.
This too is important for your organization’s software supply chain integrity, too. Internal packages have recently been susceptible to dependency confusion attacks. A white hat hacker sourced the names of internally developed packages at Shopify and Apple and then tricked these companies’ internal build tools into downloading a public version of these packages rather than the internal package. With the Tidelift Subscription, you will now have more visibility and control over your team’s internally developed packages. You could use this information to inform where to download packages from.
#3: Create exceptions for security vulnerabilities
If Equifax had addressed CVE-2017-5638, they could have stopped using the vulnerable release of Apache struts that caused the now infamous breach. Using the Tidelift Subscription’s vulnerability database, we will flag for you when an approved release is affected by a vulnerability, show you where it’s being used throughout the organization, and work with the maintainer to provide a recommendation on how to resolve the issue. You can triage it once centrally so that your development teams get quick feedback on how to resolve the vulnerability. You’ll even be made aware of these vulnerabilities for projects in your organization that aren’t receiving active maintenance.
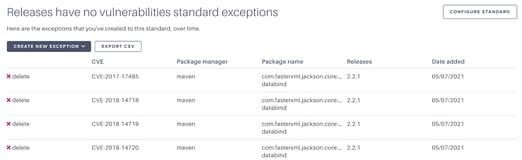
However, we have an opinion at Tidelift that developers don’t always need to stop using a package release if it’s vulnerable. Sometimes the package isn’t being used by your team in a way that makes you vulnerable (perhaps the projects are only distributed internally and the package is susceptible to a denial-of-service attack). In other cases, it’s OK to accept the risk of a minor vulnerability when there’s no alternative readily available. In these cases, you can create exceptions for vulnerabilities.
Wondering what’s approved for use but still vulnerable? You can view all created exceptions from Standards > Security > View exceptions and exceptions can also be audited in the activity feed.
So those are three ways to help keep your supply chain safe. But that’s not all! I have a quick rundown of other great updates from this month that all subscribers can take advantage of today:
- Streamlined CI/CD integration. You can now choose to integrate all of your projects in CI/CD with Tidelift with a single API key. Get started by going to Integrations > CI/CD.
- Set expiration dates for all packages. When it’s time to stop using a package, it’s typically helpful for development teams to have some time to migrate to a new version or package. You can now change the status of an approved release and set a future date on which it should be denied in your catalog. Developers will receive feedback in CI/CD that they’re using a package that’s set to expire. You can change statuses from a package page.
- New location for seeing where open source is used. It’s now easier than ever to see where open source releases are being used across your organization. From a package page, just select “usage” and you’ll see a breakdown by project of which releases are being used.
- Reports can now be re-generated and downloaded on demand from the reports page. There are reports available to export key data from the Tidelift Subscription and share with other stakeholders in your organization. Select Reports in the left-hand menu and generate the report you’d like!
If you would like to experience these great updates yourself, you can take advantage of a 14-day free trial now. This is a full-featured trial. You can get a software bill of materials for your projects or start creating your organization’s open source catalog today!
---
Before we conclude this month’s Pupdate, I must introduce you to one of the Tidelift pups. This is Buttercup who lives with Amy Hays from our marketing team. Buttercup is a total sweetheart, but she has developed a reputation of sleeping through most Tidelift meetings. I’m pretty sure the whole company has heard her snoring.



 50 Milk St, 16th Floor, Boston, MA 02109
50 Milk St, 16th Floor, Boston, MA 02109