Today we’re going to go through how leading customers integrate Tidelift’s validated open source intelligence into their tools and processes, in order to proactively detect latent risk, move to safer components, and build a healthier and more secure open source software supply chain.
What is Tidelift’s validated open source intelligence?
For organizations that rely heavily on open source software, but struggle to understand how specific open source components might make them more susceptible to vulnerabilities or attacks, Tidelift has built a unified, cross-ecosystem model for providing insights and intelligence about the secure software development practices of millions of open source packages.
More and more organizations are adopting the approach of proactively evaluating open source software, however the information needed to undertake this work can be extremely time consuming, and sometimes impossible, to gather. There is no centralized location that organizations can use for research and most of the information lives only with the maintainer(s) behind the project, when it is captured at all.
Tidelift partners directly with the maintainers of thousands of the most-relied-upon open source packages and pays them to document and validate the secure software development practices they follow—including release guidance, vulnerability reporting and disclosure policies, licensing information, and more.
These insights are critical for understanding the risks associated with a specific open source package. With Tidelift’s validated open source intelligence, organizations can reduce time spent researching and analyzing packages and make better decisions about which packages to rely on for their applications. Taking proactive steps to minimize the likelihood of being impacted by vulnerabilities is a significant improvement from the current status quo of waiting for vulnerabilities to occur and then patching them reactively.
What do organizations do with this intelligence?
We designed our open source intelligence to be a flexible source of data about how open source is developed, maintained, and adheres to secure software development practices, anticipating that customers might want to use it in several different ways. Here are the most common ways organizations are using Tidelift open source intelligence today:
- Researching new open source packages before bringing them into the organization
- Implementing ongoing monitoring for the open source software in use
Researching new open source packages before bringing them into the organization
The best way to reduce future risk in your organization is to build with more secure and better maintained components to begin with. Before bringing new open source components into your organization, you should be able to answer questions such as:
- Does it conform to my organization’s license policies?
- Is it actively maintained or is it deprecated?
- Are the maintainers actively responding to security issues?
- Are the maintainers producing new releases?
- Are the maintainers supported by a foundation, a company, or other income sources?
With Tidelift’s open source intelligence, organizations can easily answer questions like these about the secure software development practices of millions of open source packages. For thousands of the most-relied-upon open source packages, we pay maintainers to meet enterprise level security and maintenance standards, including standards aligned with the NIST Secure Software Development Framework, and keep their packages maintained to those standards into the future.
Often, the decisions a development team makes about bringing in new components leads to challenges managing open source health and security post-deployment, which in turn can lead to business continuity concerns. Teams that use Tidelift open source intelligence to research packages before bringing them into the organization can minimize unnecessary risk and rework down the road.
Implementing ongoing monitoring for the open source software in use
In the previous section, we covered the research process that goes into approving software for your organization, and how Tidelift’s open source intelligence can get you the information you need in order to make smarter decisions about bringing new packages into your application in the first place.
It is important to understand that this is not a “set and forget” task. Open source packages can change licenses. Maintainers can walk away from a project if they’re not being paid for their work. Direct and transitive dependencies can cause an issue-free component to have problems when used in production. What once was the best of breed framework for doing something can fall out of favor, while its maintainers move on and the project is deprecated. These are all important leading indicators to the potential of an open source component being compromised by a vulnerability.
Building on healthy, secure open source software requires on-going monitoring for updates and changes that impact the packages you use. Our customers are using Tidelift’s open source intelligence in their ongoing monitoring workflows to stay informed about the packages they use, and get early warning when changes take place that might make a package risky to continue using in their applications.
Where do organizations integrate Tidelift open source intelligence?
We have designed our open source intelligence capabilities to be flexible to ensure simplicity and ease of integration into your organization’s existing workflows.
Here are some of the most common places organizations integrate Tidelift open source intelligence:
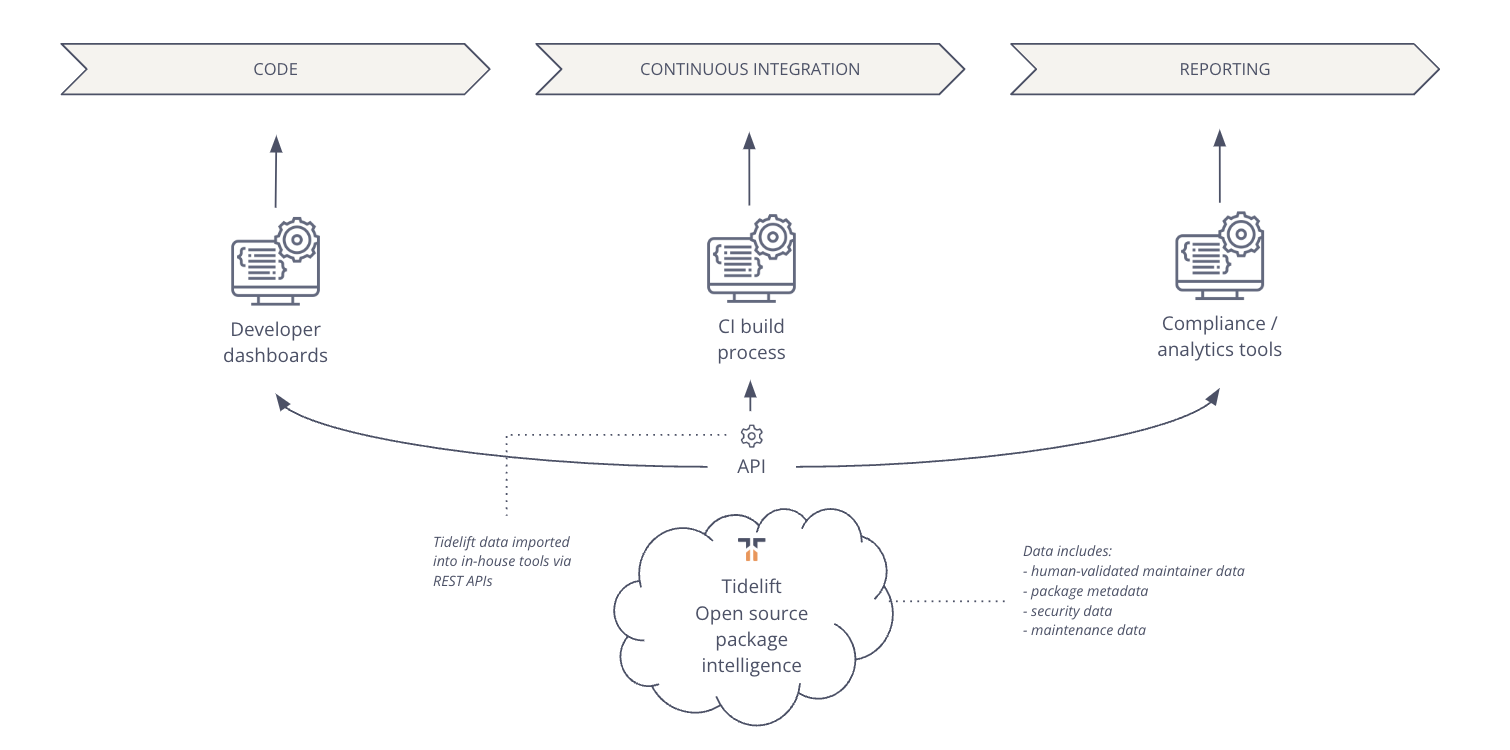
- For open source approval workflows that feed into developer dashboards
- As part of the continuous integrations pipelines to augment other checks
- Into internal reporting, business intelligence, and compliance analytics tools
For open source approval workflows that feed into developer dashboards
Most organizations have some basic processes in place to evaluate open source packages before they are approved for use. Tidelift’s open source intelligence capabilities significantly improve this evaluation process by bringing unique insights to the process. Below we describe how best to bring Tidelift’s insights into existing workflows.
An organization with a small volume of open source package reviews
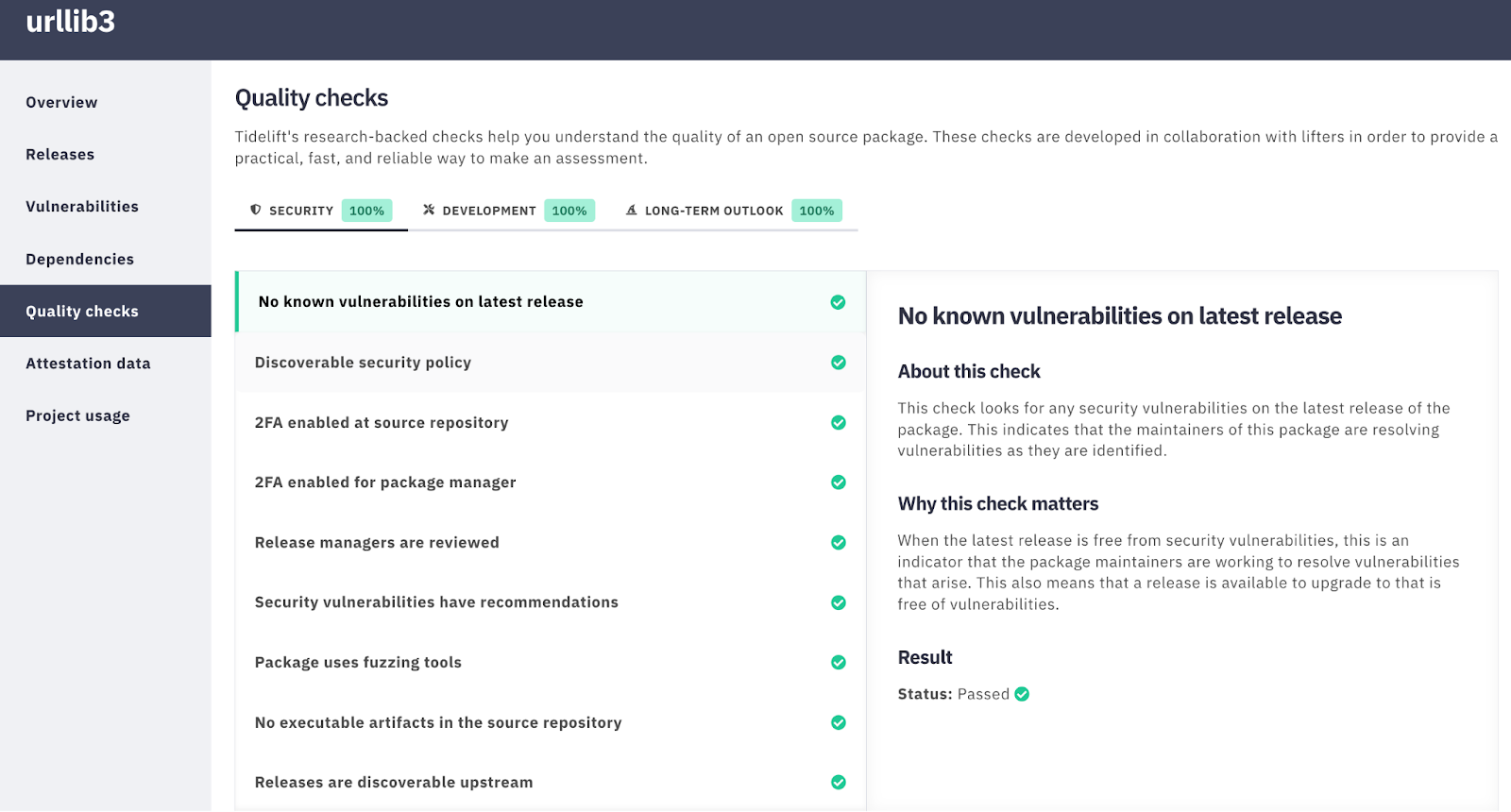
If your organization is just doing periodic review, whether by the security team, the legal team, or the Open Source Program Office (OSPO), Tidelift makes it easy to get answers about license type, version information, the maintainer(s), the software development practices a package is following, and more—just by looking up the package in the Tidelift user interface. Tidelift evaluates nearly all of the packages our customers use against a variety of metrics, and presents this information in an easy to use interface.
Figure 1: Example of open source package intelligence via Tidelift web UI
An organization with a high volume of open source package reviews
For organizations that need a higher volume of access, or just don’t like clicking around UIs, Tidelift also provides this data via a simple REST API that can be called from any programming language and integrated into the requests that are already being handled.
Using the API to access Tidelift’s open source intelligence can give you access to the same kinds of checks you’d find in the UI to help make smart decisions, including:
- The license of the package
- Whether it shows maintenance activity, or whether it’s deprecated
- Whether it’s responsive to security issues
- The release history of the package
- Whether the maintainers are receiving income for their work
and more
Figure 2: Example of open source package intelligence via Tidelift API
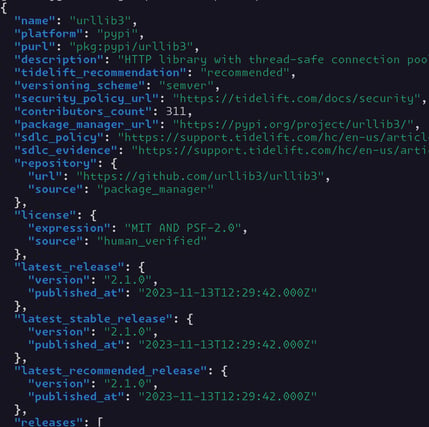
The API output also includes all of the underlying criteria that goes into data fields for deeper analysis.
In addition to using these insights to evaluate and approve which open source packages developers should be using, this data from Tidelift can also be used to make suggestions to developers. If, for example, your developers are looking for a new python HTTP library, using Tidelift’s open source intelligence, you can suggest the most popular, most well maintained packages that align with the internal requirements.
As part of the continuous integrations pipelines to augment other checks
Getting important information directly in front of developers as they’re developing is a key way to increase developer velocity.
Tidelift makes it easy to bring information directly to developers so they can see when their dependencies have risks, and determine best how to address them. By putting Tidelift’s package and release intelligence in front of developers, they can make better decisions directly.
Separately, many organizations check their software’s risk level in their continuous integration/continuous delivery pipeline. Each time they build their software, they assess it for issues using various scanning tools, and feed those results into their risk analysis or business intelligence tooling.
Tidelift brings proactive indicators of future risk into this process. When running a build in your CI/CD platform, you can also query Tidelift for information about the components in the build. This information can then augment other reports, and be imported into the same tooling, whether that’s your DevSecOps’s prioritization pipeline, your issue reporting tool, or your internal dashboards.
Into internal reporting, business intelligence, and compliance analytics tools
Customers have incorporated Tidelift into their business intelligence and risk analysis tools. These tools draw data from diverse sources, including software scanners, public repositories such as the National Vulnerability Database (NVD), and internal business metrics. The resulting insights are commonly utilized by CISOs and C-suite executives to understand the organizational risks associated with the software they consume and build, and by engineering leads as they plan and prioritize upgrades.
Insights from Tidelift such as the security standards being implemented, along with license information, and the ability to identify unmaintained or deprecated packages are valuable for organizations to assess not only current, but latent and future risks associated with open source software. Tidelift works with organizations to sequence our APIs such that their business intelligence and risk analysis tools are continuously updated with the latest insights on all of the open source software they might be interested in.
Learn more
As we move forward, it is becoming increasingly critical to implement both proactive and reactive strategies to manage risk and improve the health and security of the open source software supply chain. It is important to identify existing vulnerabilities and remediate them, but it is equally important to minimize the likelihood of not being impacted by issues in the first place. Watch this demo to learn more about how you can use Tidelift’s validated open source intelligence to make informed decisions on which packages and versions to use for development.


 50 Milk St, 16th Floor, Boston, MA 02109
50 Milk St, 16th Floor, Boston, MA 02109